Cloud Compliance
Who Does HIPAA Affect?
HIPAA, the Health Insurance Portability and Accountability Act, includes privacy and security rules, enforced by the US  government to uphold regulatory standards, for the protection and safety of patient data.
government to uphold regulatory standards, for the protection and safety of patient data.
Individual patients are directly touched by HIPAA in a positive way, by having their identity and their electronically housed personal and sensitive health information protected.
Business organizations tasked with processing, maintaining and storing protected health information (PHI) are responsible for following and meeting the rules set forth by HIPAA with their infrastructure and solutions. These organizations include those providing healthcare treatment, payment or operations, are known as Covered Entities (CE), along with their Support and IT Service providers, and are considered the Business Associates (BA) of the CE.
We Can Help You with HIPAA
BVoIP, through our partners, offers a solid platform to build your HIPAA compliant solution. Whether maintaining protected patient and medical data, or managing IT services for those who do, we can enable your efforts with the highest security and  reliability to help you address the challenges of HIPAA.
reliability to help you address the challenges of HIPAA.
With multiple, geo-diverse data centers, our controlled, highly available and concurrently maintainable environments are excellent for the protection of vital research and medical data. Flexible and robust, we incorporate large scale power and cooling, while minimizing unused space to create compliant ready, high density environments, perfectly suited for today’s high-performance, ‘super’ compute and storage devices.
Who Does PCI DSS Affect?
The Payment Card Industry Security Standards (PCI) and Data Security Standards (DSS), or PCI DSS, are security and data protection compliance rules developed, maintained and managed by the PCI Security Standards Council, an international  forum comprised of leading credit card institutions.
forum comprised of leading credit card institutions.
PCI DSS standards protect consumers, and financial and credit card institutions by standardizing the secure treatment of cardholder data from the moment that credit card information is entered into a payment system; through payment authorization, processing and bank settlement.
Business organizations tasked with protecting cardholder information are responsible for following and meeting the protection standards set forth by PCI DSS with their hardware, applications, systems and solutions. These organizations include merchants, payment processors, financial institutions, or any group storing, processing, and transmitting consumer credit card data.
The risks are high for companies or organizations handling such data that choose not to adhere to PCI DSS, with costs being exorbitantly high if a consumer data breach affects their systems or infrastructure. Associated breach costs can take a toll on a company’s financials with large banking fines and retribution packages, as well as harm to business and brand reputation. PCI DSS standards are strictly enforced and investigated collaboratively by a range of law enforcement agencies and the affected Credit Card associations.
We Can Help with PCI DSS
BVoIP, through its partners, offers a solid platform for you to build your PCI DSS compliant solution. Whether taking payments, processing payments or hosting clients who do, we can enable your efforts with the highest level of physical, network and technical security. With a strong up-time record and around the clock network and support personnel, we can  ensure reliable service 24/7/365.
ensure reliable service 24/7/365.
BVoIP's upstream partners are PCI DSS v. 2.0 validated service providers, thus we maintain compliance for our Infrastructure as a Service (IaaS). In addition, each of our US and EU facilities are also SOC Type 2 audited data centers, offering the highest level of protection and a global footprint to back up and connect your critical data across multiple regions.
BVoIP's Public and Managed Private Cloud are each third-party audited and offer a scalable, yet secure, PCI DSS solution.
Cloud Security
Firewalls
As internet security concerns continue to rise, it’s critical for businesses to take necessary precautions to protect their online services and transactions. BVoIP understands these concerns and begins its security measures at the cloud level. Our redundant enterprise-class firewalls are the first line of defense and are at the core of our service offerings.
PBX Automated Anti-Hacking Security Features
3CX Phone system has a security menu that is preconfigured with security settings to attempt SIP hacking of the phone system as well as bad password attempts and a large volume of traffic that is considered unusual. You can modify the settings in this menu as you see fit but make sure to consider your options carefully!
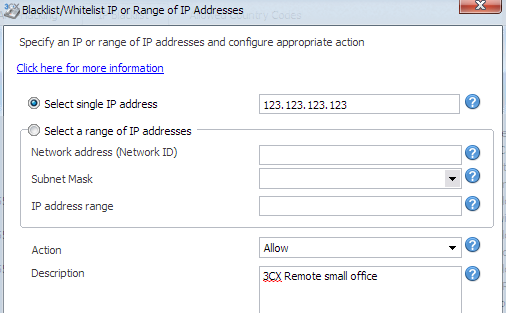
3CX Phone system allows you to also whitelist and blacklist IP addresses. All traffic originating from the whitelsit IP addresses will be allowed through unchecked by the anti-hacking features. All traffic originating from blacklist IP addresses will be dropped immediately.
3CX Phone System also allows you to enable traffic to the specific countries that you expect to make outbound calling to in an effort to limit call fraud should one of your extension credentials be comprimised.
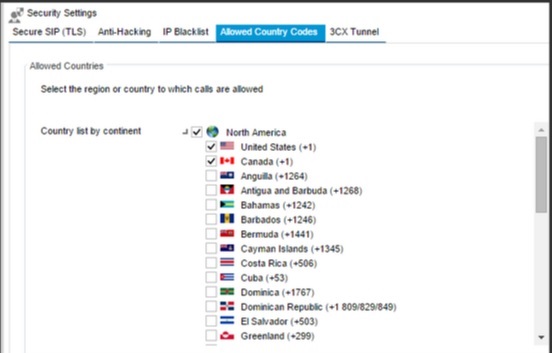
Secure SIP (TLS)
3CX Phone System can establish secure SIP connections if desired. To enable this you to create a private key and certificate. Note that this feature does not work with all phones.
SBC Security Features
Security is important issue addressed by our Session Border Controllers (SBC's). DOS, DDOS, fast and slow attacks can be controlled. Our SBC's protect the Proxy and Registrar server from malformed SIP packets and Avalanche Restart effect as described in RFC5390.
DDoS Protection
Threats of DDoS attacks continue to rise and the businesses that rely on the internet to reach their customers are increasingly at risk of encountering problems related to these attacks. While there are varying degrees of DDoS protection offered by service providers, you have to choose the right options to your unique business. Weighing both the economics and risk levels becomes important as our business grows and becomes more visible.
Our best effort DDoS mitigation offers you peace of mind knowing that we're watching over your network traffic and taking action against attacks, keeping your servers online and your business moving. Our DDoS mitigation services comes standard with all of our services, and provides protection against the majority of small and medium attacks as a whole.
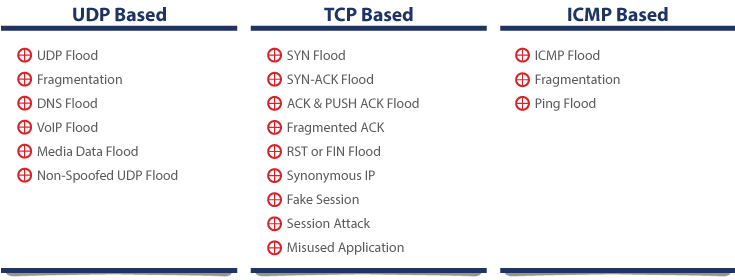
We offer protection against several DDoS Attacks:

Server Drive Encryption
If required we have the ability to enable server level hard drive encyrption utalizing Microsoft's BitLocker Technology. This feature set is built into Microsoft's Windows Server operating systems.
Cloud Compliance
BVoIP's cloud facility vendors are SOC 2 audited and a Payment Card Industry Data Security Standard
(PCI DSS) Validated Services Provider. BVoIP's heightened security measures allow you to bypass the expense of a complete security audit and, instead, use our vednor's reports to meet some of your own guidelines.
The physical security standards we meet also help you address any industry-specific regulations you might be sub


ject to such as the Sarbanes-Oxley Act (SOX), Gramm-Leach-Bliley Act (GLBA), or Health Insurance Portability and Accountability Act (HIPAA). And if you are taking online payments, you can leverage our physical security measures to meet some of your own PCI requirements.
Cloud Redundancy
Network
Engineered to provide the maximum amount of speed and reliability, BVoIP's network delivers persistent speeds for your entire traffic flow. The backbone is directly connected to our Tier 1 providers through redundant dedicated ten-gigabit uplinks and is managed by our group of certified vendors which is managed by our network operation center (NOC) to ensure uptime is consistently upheld.
By keeping usage to no more than 50 percent of our overall capacity, we are able to maintain a reliable, rapid network in the instance of an Internet routing disturbance. In the occurrence of a network provider going offline, your traffic will automatically be routed to another available provider during the outage. This allows your online presence to remain undisturbed.
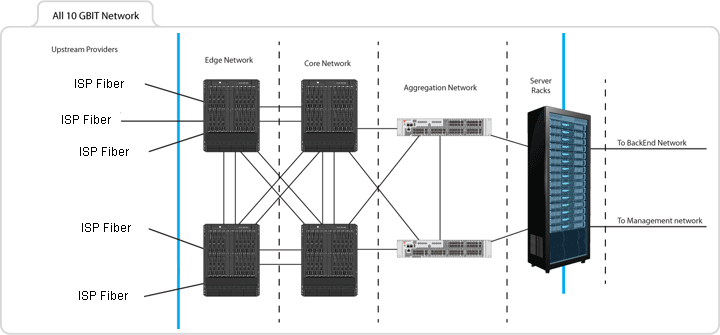
Bandwidth

BVoIP utlizes premimum bandwidth from multiple Tier 1 carrier providers combined with Border Gateway Protocol (BGP), BVoIP delivers information flow redundancy and guarantees your traffic continually follows the best routing path(s) in all of our facilites. By creating diverse redudnant path availability, your data constantly flows, your connections remain concrete and your response times are imrpovded, avoiding latency. Furthermore, our highly trained, certified, onsite staff located inside our full service cloud facilities analyzes traffic 24x7 to uphold the utmost network performance levels.
Redundant Firewalls / Routers

The high-end redundancy features of our firewalls provide business continuity and disaster recovery at levels of reliability usually reserved for larger enterprises. Advanced features include active-passive failover for distributing or load sharing outbound WAN traffic and hardware failover for automatically activating a passive appliance to assume responsibility for forwarding traffic. We utalize the active-passive failure approach at all of our cloud facilities.
Redudant SBC's (Session Border Controllers)
We make sure that we have geographic redudancy for our Session Border Controllers which is critical in our remote phone infrastructure design. Utlizing SIP SRV records remote devices should be able to autmatically fail over between SBC's in order to maintain the uptime you expect. We also utalize for low TTL DNS platforms in order to provide the ability for us to update our infrastructure records should we need to make a major change without having to re-provision or program remote devices.
Warm Spare Continuity Approach
With our warm spare approach, backups can be virtualized either locally or remotely in one our sister cloud facilities, in mere seconds, with the click of a button. Even while virtualized, systems can continue a normal backup schedule to both the local backup system or one of our sister cloud locations.
The advantages to Instant Virtualization are many. Should a physical blade experience server failure, or the like, its systems may be virtualized instantly. With the system now virtualized in the Cloud, you may operate “business as usual” and we will have the time and resources to fix its server issue without compromising any data or incurring any downtime.
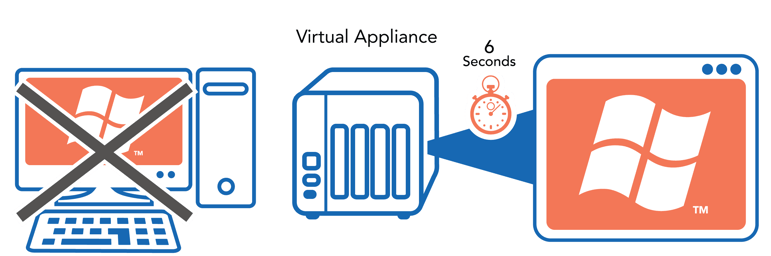
Cloud SBC - Session Border Controller
SIP – Why NAT and/or PAT is Insufficient?
There are a number of fundamental reasons why simple NAT and PAT are insufficient to resolve NAT traversal issues for VoIP traffic in general and for SIP
signaling specifically. A small subset of the reasons:
- The SIP Standard requires a number of header fields to be specified, some of which need to contain the IP Address where responses need to be sent to. Since NAT and PAT operate only on the IP headers, and not on the UDP Payload, the WAN-to-LAN device does not address this issue at all.
- SIP does not only perform the tasks of setting up, adjusting calls, and tearing down calls, but also incorporates the media codec negotiation phase inside an embedded protocol called SDP (Session Description Protocol). Again, the WAN-to-LAN device does not address this additional content at NAT or PAT level.
Most users own NAT based routers/firewalls that make the roll-out of an IP based network of IP phones or phone adapters a nightmare if you don’t have the right tools. The fact that VoIP protocols encapsulate each device’s IP address in the session layer packet and firewalls won’t allow any session originated
from the public Internet to traverse to internal-protected network. This results in all sorts of problems like no audio or one way audio.
Some attempts to resolve this issue such as STUN or reconfiguring end-users routers or firewalls may not always work and will become a support debacle when facingdifferent types of NAT across different firewall and router manufacturers. Some systems provide a tunnel or SIP Proxy applicationas an “answer” to this issue but this option has limitations, especially when dealing with remote users that need to connect back to a SIP server. Is this really the best answer?
A Better Answer! - SIP proxy/Session Border Controller (SBC)
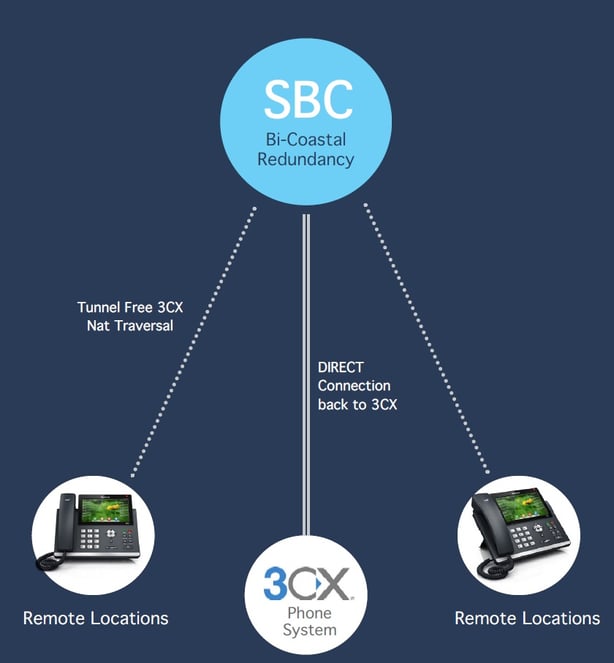
The BVoIP SBC is a carrier grade solution that can provide service to tens of thousands of endpoints. Phones or other SIP devices will have a configuration field for a “SIP proxy” server and port - when pointed to the SBC, all SIP packet rewriting for NAT support is handled automatically. This eliminates the need to use STUN,  TURN, ICE, VPN, Tunnel or any other method to handle NAT.
TURN, ICE, VPN, Tunnel or any other method to handle NAT.
The Session Border Controller allows VoIP sessions to succeed when one or more VoIP endpoints (such as analog phone adapters, gateways or IP phones) are in a NAT environment. Our offering takes all of the mess out of connecting remote devices back to a SIP server and greatly simplifies your deployment! This offering is designed to work as an intermediary between endpoint devices made by Yealink, Cisco, Snom, Polycom, Fanvil and more!
Our SBC solution is a simple solution for BVoIP partners to deploy their systems with a minimum of support and intervention on the customer premise and totally automates the NAT traversal process. In addition to NAT traversal, security is another important issue that is addressed. DOS, DDOS, fast and slow attacks can be controlled by the SBC to help protect the 3CX server from malformed SIP packets and Avalanche Restart effect.
Public & Private Cloud
Service is Key
Finding a trusted cloud vendor with premium IT solutions at an affordable price can certainly support your efforts to engage  your clients, while supporting their growing IT needs. Offering an OpEx friendly payment option when they are purchasing services can result in a big smile on the client’s face, and a signed contract in your pocket.
your clients, while supporting their growing IT needs. Offering an OpEx friendly payment option when they are purchasing services can result in a big smile on the client’s face, and a signed contract in your pocket.
As a Managed Services Provider (MSP) or IT Services Provider (ITSP), your goal is to keep your clients happy by giving top notch service, finding them best in breed technologies, and getting those solutions at the most affordable price. What if you could focus your time on providing amazing service, and feel confident that your client will still be smiling tomorrow, with a sound infrastructure foundation, no upfront costs and a simple monthly payment?
Bank on our Solutions
As a trusted provider, BVoIP aggregates and offers a scalable, reliable and affordable platform for your client’s infrastructure, so you can concentrate on what you do best; managing their services. Our portfolio of highly desirable, premium solutions,  including Public & Private Cloud PBX, mean you can bank on servicing your client accounts for years to come. With multiple, geo-diverse data centers and 24/7/365 client access, your clients are provided a secure, redundant and reliable offering for you to manage their services.
including Public & Private Cloud PBX, mean you can bank on servicing your client accounts for years to come. With multiple, geo-diverse data centers and 24/7/365 client access, your clients are provided a secure, redundant and reliable offering for you to manage their services.
Growing infrastructure can be a budget challenge for any client. The ultimate OpEx friendly alternative for your clients, BVoIP provides acces to own our ‘best in breed’ inventory of servers and additional equipment from such brands as SuperMicro®, Brocade®, and Dell SonicWall®.
You can score big with your ‘refresh ready’ clients by offering them a quick and easy way to scale and deploy shared or dedicated resources with little upfront investment. Save them CapEx costs on hardware, software licensing, and complex installations with our cloud PBX solution. Affordable and flexible, BVoIP can effectively burst on demand, and quickly deploy  additional resources as needed.
additional resources as needed.
Your clients depend on you to provide reliable and dependable service for the management of their IT. Why not offer them the same when it comes to their communications environments.
At BVoIP, you and your client are not ‘just a number.’ We provide each BVoIP partner with a dedicated onboarding expert for you and your MSP opportunities, giving that ‘concierge connection’ inside our company, and helping to make sure you both walk away happy.
Locations
We have our infrastructure strategically located in North America, UK & Europe, and Australia & New Zealand. So if you have clients in one part of the world or are globally distributed you only need one vendor to serve them all!
Infrastructure
 BVoIP delivers Public and Private Cloud solutions specifically designed for real time voice and video callaboration that feature highly reliable, efficient, and redundant infrastructural systems. With servers housed in the full service, enterprise-grade data centers, our vendor cloud facilities include the state-of-the-art security, available 2N power distribution, and cooling efficiencies inherent to choosing the "right" facilities. These fully redundant systems enable BVoIP solutions to offer some unique advantages in the cloud market space, and enable you to reap the benefits. With BVoIP, you're not just getting a great cloud solution; you're getting a cloud solution that resides in world-class data centers.
BVoIP delivers Public and Private Cloud solutions specifically designed for real time voice and video callaboration that feature highly reliable, efficient, and redundant infrastructural systems. With servers housed in the full service, enterprise-grade data centers, our vendor cloud facilities include the state-of-the-art security, available 2N power distribution, and cooling efficiencies inherent to choosing the "right" facilities. These fully redundant systems enable BVoIP solutions to offer some unique advantages in the cloud market space, and enable you to reap the benefits. With BVoIP, you're not just getting a great cloud solution; you're getting a cloud solution that resides in world-class data centers.
Connectivity
BVoIP's various networks delivers high-performance bandwidth with direct connections to major Internet Service Providers. But it is much more than that. Featuring a 60+ Gbps capacity and 10GigE transit and peering links, the network is built to perform. It also includes a 10 Gigabit Ethernet to ensure a constantly stable, secured, scalable and redundant cloud environment.

Network Features Include
- 0% Packet Loss On Our Network
- Maximize the performance of your dedicated server with a network that eliminates any potential data degradation.
- Multiple internet backbone connections
- Redundant network architecture load balancing system with Border Gateway Protocol (BGP) for no single point of failure.
- Geographically diverse fiber paths
- Two separate trenches for carrier fiber help keep your network service online.
- Per server private VLAN (virtual local area network)
- Allows for creation of a private network within the larger network, giving you greater security, privacy and performance.
Servers
BVoIP looks to offer you the best systems and hardware available to support your needs. BVoIP is standarized on high-quality hardware from Supermicro & Del. We are proud to include their product lines in our solutions.
Supermicro & Dell Benefits:
- Optimized designs to improve server operation
- Tested and certified products to help ensure performance
- First-to-market strategy to provide latest technologies
- Customized product lines to support high density and high availability hosting
Additionally, with the wide-range of servers and pricing Supermicro & Dell are able to offer, we can keep our costs down and pass the savings on to you through our competitively priced cloud solutions.