Note from our CEO on the 3CX Windows & MAC App Compromise
Background Info
Crowdstrike Analysis
https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
SentielOne Analysis
Toydl Analysis
3CX Formal Acknowledgement
https://www.3cx.com/blog/news/desktopapp-security-alert/
https://www.3cx.com/blog/news/desktopapp-security-alert-updates/
https://www.3cx.com/blog/news/chrome-blocks-latest-msi/
https://www.3cx.com/blog/news/pwa-vs-windows-legacy-app/
https://www.3cx.com/blog/news/uninstalling-the-desktop-app/
https://www.3cx.com/blog/news/security-incident-updates/
Currently known vulnerable version numbers for the 3CX platform:
Windows:
- 3cxdesktopapp-18.12.407.msi
- 3cxdesktopapp-18.12.416.msi
Mac:
- 3CXDesktopApp-18.11.1213.dmg
- 3cxdesktopapp-latest.dmg
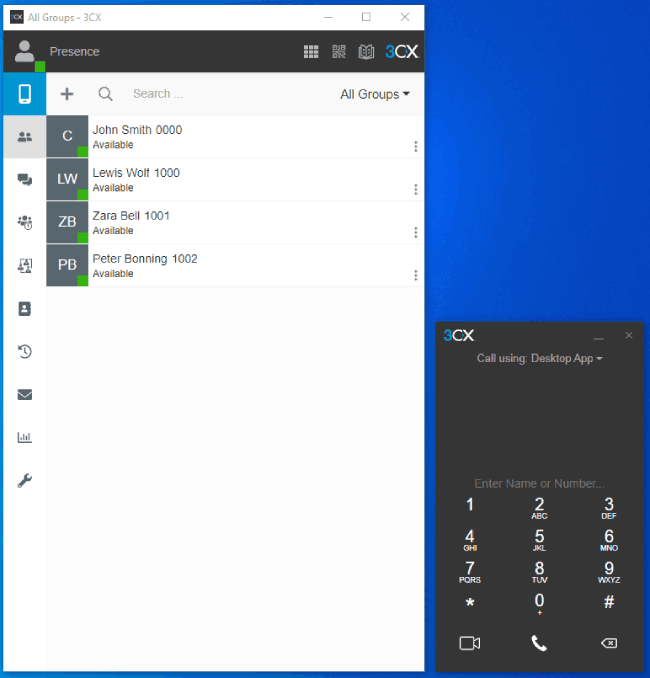
If your phone Windows App looks like the one, below you are OK 👍
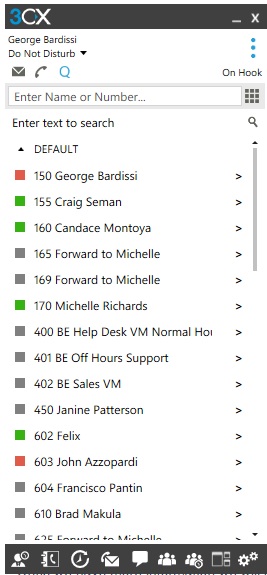
If your windows app looks like the image below, then you might have an issue! ⚠️
If these versions are indeed installed it is recommended to uninstall them!
There are no concerns with the web client, which is browser-based, or the iOS / Android apps.
Here is a quick uninstall script (please test before mass deployment)
We created a PowerShell script that you should be able to deploy with any RMM platform you use to mass uninstall the v18 Windows Client - Click Here to Uninstall 3CX Desktop App
The Good News
bvoip's stable system version is v5 of the PBX platform and the affected version is v7. All existing and new accounts remain on v5. We are in the final stages of validating v6 at the moment and have not even considered v7.
Also, if you are running older versions like v12, v14, and v16 then you are also unaffected.
Here is an offer from Huntress
Also, our friends from Huntress who work closely with the MSP Community are offering a 30-day no-cost option to allow you to deploy their MDR solution and they are monitoring for any abnormal activity across their partner base. You can CLICK HERE to learn more.